Secure Raspberry Pi Access: Remote.it, VPN & AWS VPC Guide
In today's increasingly connected world, are you wondering how to safely unlock the full potential of your Raspberry Pi from anywhere? Securing your Raspberry Pi, especially when accessed remotely, is paramount for protecting your data and maintaining the integrity of your projects, and fortunately, it's entirely achievable.
The Raspberry Pi, a marvel of compact computing, has become a staple for hobbyists, developers, and businesses alike. Its versatility is undeniable, but with great power comes great responsibility particularly when it comes to security. The ability to access your Raspberry Pi from any location offers unparalleled convenience, opening doors to remote monitoring, automation, and various other innovative applications. However, this convenience hinges on establishing a robust and secure connection.
Before we delve deeper, let's clarify a few important terms:
- VPC (Virtual Private Cloud): A logically isolated section of a public cloud, such as AWS, allowing you to launch resources in a network that you define.
- Remote IoT: IoT devices that are located in a different physical location from the user or server.
- P2P SSH (Peer-to-Peer Secure Shell): A secure connection method that bypasses intermediary servers, connecting devices directly.
The following table provides a comprehensive overview of the crucial aspects related to securing your Raspberry Pi, including the steps to establish a secure connection, potential challenges, and available solutions.
| Aspect | Details | Importance |
|---|---|---|
| Security Fundamentals |
| These are the foundation of a secure setup. Default settings are a major security vulnerability. Up-to-date systems are less vulnerable. Firewalls control access, SSH provides secure remote access. |
| Remote Access Methods |
| These methods provide various ways to securely connect. Each has its strengths and weaknesses, but all prioritize security. |
| Connecting to AWS VPC |
| Securing your Pi within an AWS VPC enhances security and allows integration with other AWS services. Encryption protects your data. IAM roles manage access control. |
| P2P SSH Implementation |
| P2P SSH offers the benefit of direct, secure connections that circumvent potentially vulnerable central servers. |
| File Sharing |
| These protocols provide a secure way to access and share files, which is often a core requirement for remote access. |
| Common Challenges |
| These are common obstacles and require attention. Good IP management and a secure configuration are essential. |
| Best Practices |
| Following these practices significantly enhances the overall security posture of your Raspberry Pi. |
For more details and in-depth guides, refer to the official documentation on the Raspberry Pi Foundation website.
One of the primary methods for secure remote access to your Raspberry Pi is through Secure Shell (SSH). With SSH, you can establish an encrypted connection to your device and execute commands remotely, manage files, and even access graphical interfaces. The process, though straightforward, requires careful attention to detail to ensure a secure setup.
Before delving into the specifics, it's important to acknowledge the inherent security vulnerabilities of the Raspberry Pi out of the box. The default settings, including the username and password, are widely known, making them a prime target for malicious actors. Therefore, the first and most crucial step is to change the default password immediately upon setting up your device. Additionally, it is recommended to disable the default "pi" user and create a new user account with strong credentials.
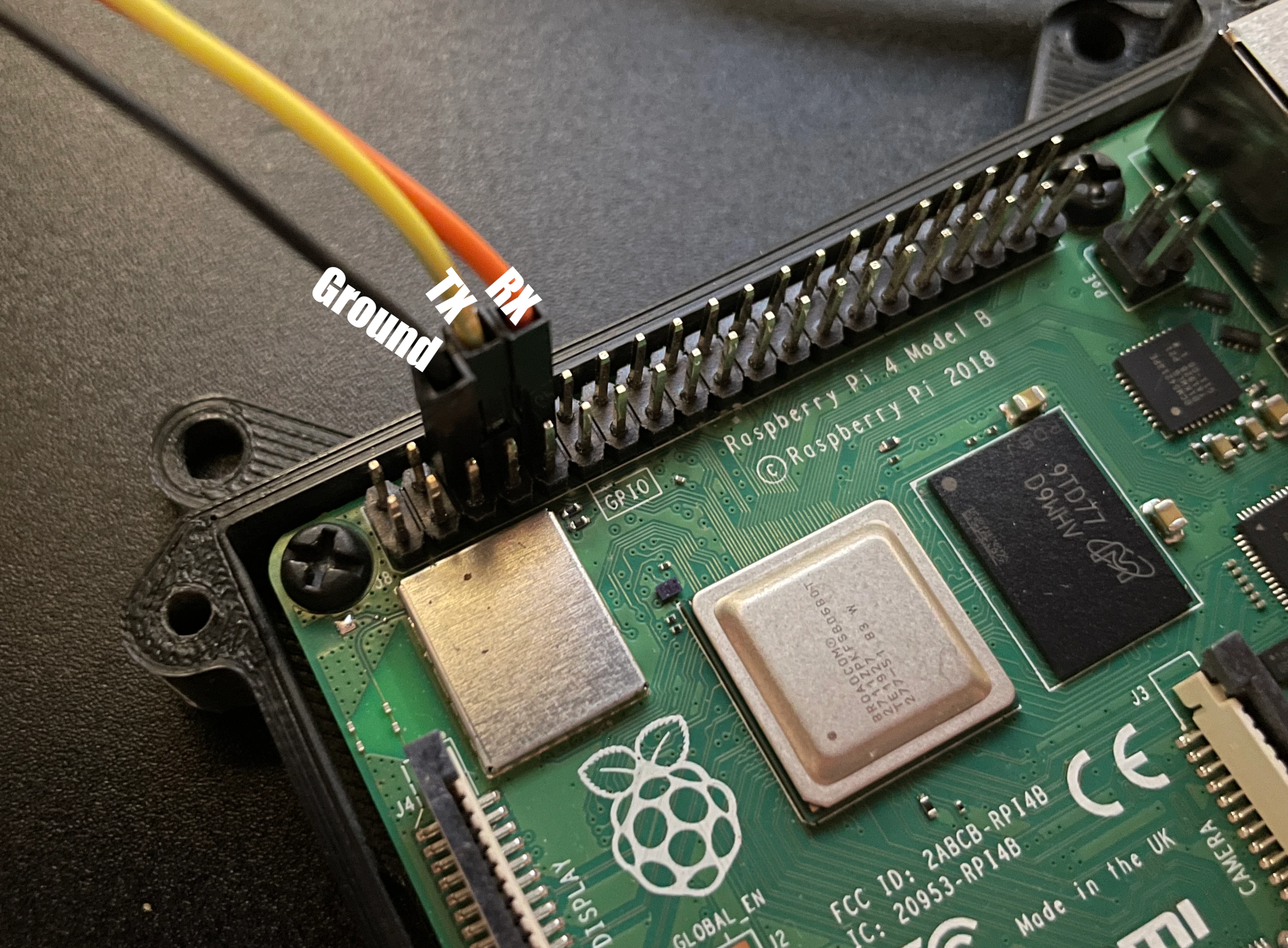
To get started, youll need to enable SSH on your Raspberry Pi. This can be done in a few different ways. If you have access to a monitor and keyboard connected to your Pi, you can enable SSH through the Raspberry Pi configuration tool. Alternatively, if you have already set up a network connection, you can enable SSH using the command line. First, find your Raspberry Pis IP address. This is crucial because you'll need it to connect to your Pi from another device. You can find the IP address by connecting a monitor and keyboard directly to the Pi or by checking your router's connected devices list. Once you have the IP address, you can connect via SSH using a terminal or SSH client such as PuTTY (for Windows) or the built-in SSH client on macOS and Linux.
Here's a brief overview of how to set up SSH:
- Find your Raspberry Pis IP Address: This can be done by connecting a monitor and keyboard, or by checking your router's settings.
- Connect via SSH: Use an SSH client (like PuTTY or terminal) to connect to your Pis IP address.
- Enter Credentials: Use the username and password you created.
Once you are connected via SSH, you can execute commands, manage files, and even access the Raspberry Pi's desktop environment. Remember to regularly update your system using the `sudo apt update` and `sudo apt upgrade` commands to patch security vulnerabilities.
For enhanced security, it is recommended to implement a firewall, such as `ufw` (Uncomplicated Firewall), to restrict incoming connections to only the necessary ports. This will help prevent unauthorized access to your device. You can also consider using key-based authentication instead of password authentication for SSH. This involves generating a key pair (a private key and a public key), adding the public key to your Raspberry Pi, and disabling password authentication. This method is significantly more secure.
In situations where you want to share files between devices, you have several options: Network File System (NFS), Secure Copy Protocol (SCP), Samba, and rsync. Each of these services has its benefits and use cases, so understanding them will allow you to implement the one that suits your requirements.
Beyond SSH, the concept of connecting your Raspberry Pi to a Virtual Private Cloud (VPC) using AWS and a service like Remote.it or Tailscale represents a more advanced approach to secure access. These solutions offer several advantages, including:
- Enhanced Security: Your Raspberry Pi is protected by the security measures offered by the VPC.
- Simplified Connectivity: Remote.it and Tailscale simplify the process of accessing your device from anywhere, without the need to configure complex network settings.
- Scalability: The VPC environment is highly scalable, allowing you to accommodate future growth.
Remote.it and Tailscale function as intermediaries, enabling you to connect to your Raspberry Pi securely without exposing your IP address and port information publicly. They employ a peer-to-peer (P2P) service, ensuring that your data does not flow through their services, thereby enhancing security.
When using Remote.it, you must install the connect software and link your device with an account on your Raspberry Pi. Then, you can access the desktop or a shell running on your Raspberry Pi through a browser window at connect.raspberrypi.com. Tailscale, on the other hand, provides a mesh VPN, creating a secure network between your devices.
In addition to secure access, you can set up file sharing using services like NFS, SCP, Samba, and rsync. These solutions enable you to share files between devices on the local network without directly controlling the devices.
To establish a secure connection between your Raspberry Pi and an AWS VPC, you'll generally need to:
- Set up a VPC on AWS: Configure the necessary network settings, including subnets, routing tables, and security groups.
- Install and Configure Remote.it or Tailscale on your Raspberry Pi: This involves setting up the necessary configurations and creating a secure connection.
- Configure your Raspberry Pi to connect to the AWS VPC: This may require setting up VPN connections and configuring firewall rules.
- Ensure data encryption: All data transmitted between the devices and the VPC should be encrypted to maintain privacy.
- Regularly update your systems and security: Maintain the security posture of your system to stay safe.
Connecting your Raspberry Pi securely to a VPC offers a powerful way to manage IoT devices efficiently. Always make sure to stay up-to-date on the best practices.
Moreover, when dealing with remote access, it is important to understand the benefits and the challenges. Common challenges include the need to find the Raspberry Pi's IP address, and properly configure the network. Fortunately, solutions like Remote.it and Tailscale offer straightforward pricing structures, beginning with free tiers that support multiple devices, complete with key features for secure remote access.
Setting up SSH on your Raspberry Pi is easier than you think. You can enable SSH on your Raspberry Pi by following these simple steps:
- Find your Raspberry Pis IP Address: You can typically find it through your router's interface or by directly connecting a monitor and keyboard.
- Enable SSH: Enable SSH either through the Raspberry Pi Configuration tool (if you have display access) or via command line.
- Connect via SSH: Use an SSH client to connect. The format is usually ssh username@ip_address.
- Enter Credentials: Enter the username and password you set up.
Connecting your Raspberry Pi securely to a virtual private cloud (VPC) is a crucial step in ensuring the safety and efficiency of your IoT projects. Understanding how to securely connect to a VPC is essential for protecting sensitive data and maintaining reliable operations.
A comprehensive guide to securely connecting your Raspberry Pi to a remote IoT network using P2P SSH involves several steps: from initial configuration to testing. Below is a detailed guide to help you through the process. Remember that securely connecting remote IoT devices to a VPC using a Raspberry Pi involves creating a secure communication channel between your IoT devices and the cloud infrastructure.
- Set up your Raspberry Pi with the latest version of Raspberry Pi OS: Make sure its fully updated.
- Establish a secure connection: Utilize either SSH, a VPN, or a secure access service.
- Ensure Encryption: If you are transmitting data, ensure that encryption is utilized.
- Regularly update your system: Always update and patch your system for vulnerabilities.
By taking these steps, you are well on your way to creating a secure and efficient infrastructure that meets your specific needs. The best way to take your IoT journey to the next level is to keep learning and keep improving security practices.