Raspberry Pi Secure Access: Connect & Control Your Pi Remotely!
Is your Raspberry Pi securely accessible, or is it a potential vulnerability waiting to be exploited? Securing your Raspberry Pi is not just a good practice; it's a necessity in today's interconnected world.
The Raspberry Pi, a marvel of compact computing, has revolutionized the landscape of DIY electronics and the Internet of Things (IoT). Its versatility and affordability have made it a favorite among hobbyists, educators, and professionals alike. From home automation systems to media servers, and even robotics projects, the Raspberry Pi's applications are vast and continuously expanding. However, its default configuration often leaves it vulnerable to security threats, making it crucial to understand how to protect it. This article delves into the specifics of securing your Raspberry Pi, exploring different methods to ensure safe and reliable access, and safeguarding your data.
To provide a comprehensive overview of the various aspects to secure your Raspberry Pi, consider this information:
| Aspect | Description |
|---|---|
| SSH (Secure Shell) | A network protocol that allows you to securely connect to another computer or device over a network. It's a lifeline for remote access, eliminating the need for a monitor, keyboard, or mouse, especially beneficial for headless Raspberry Pi setups. |
| Raspberry Pi Connect | A secure remote access solution that allows you to connect to your Raspberry Pi desktop and command line directly from any browser. It simplifies access by eliminating the need to determine your local IP address. It is enabled by default in new installations. |
| Remote IoT VPC (Virtual Private Cloud) | A secure and reliable connection between your Raspberry Pi and a VPC, facilitating secure communication between your IoT devices and cloud services, protecting sensitive data from potential threats. |
| File Sharing Protocols | Protocols like NFS (Network File System), SCP (Secure Copy Protocol), Samba, and Rsync that enable secure file sharing between devices on the local network without direct control of the remote device. |
| VPN (Virtual Private Network) | Encrypts all data transmitted between your Raspberry Pi and the VPC, ensuring private and secure communications. |
Reference Website: Raspberry Pi Official Website
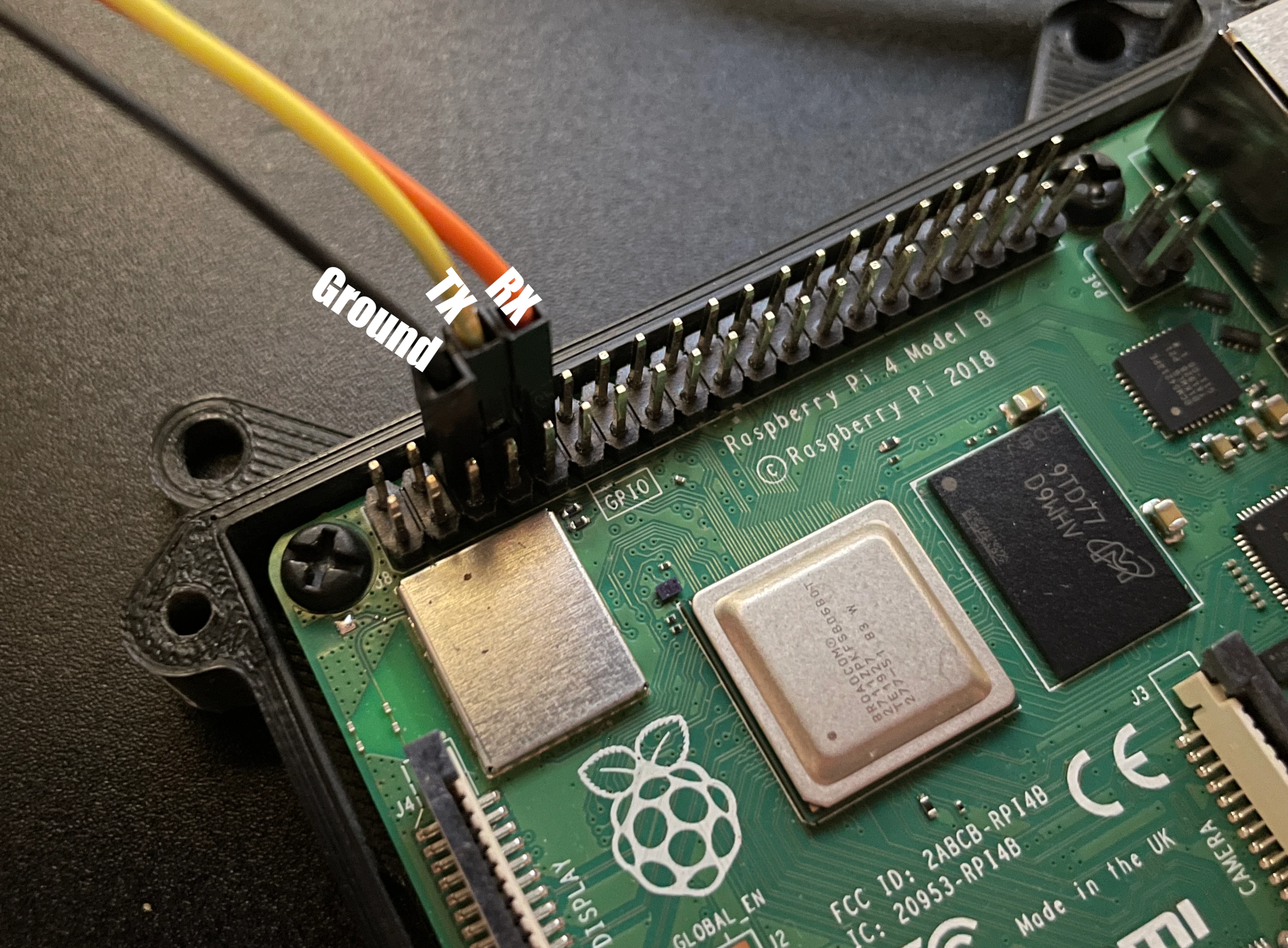
At the heart of securing a Raspberry Pi lies a fundamental understanding of how it can be accessed and controlled. The most common method is through SSH (Secure Shell), a protocol designed to provide secure remote access to a command-line interface. Think of it as a secure tunnel, enabling you to remotely execute commands on your Raspberry Pi, just as if you were sitting directly in front of it. This is incredibly useful for headless setups those without a monitor, keyboard, or mouse which are typical in IoT projects. SSH allows you to manage your Raspberry Pi from anywhere on your local network or, with proper configuration, from anywhere in the world.
To establish an SSH connection, you'll need to know your Raspberry Pi's IP address. This can be found in a few ways: if you have a display connected, you can use the terminal on the Raspberry Pi itself. Alternatively, if your Raspberry Pi is connected to your network, you can often find its IP address through your router's administration interface or by using network scanning tools on another device connected to the same network. Once you have the IP address, you can use an SSH client (like the built-in terminal on Linux or macOS, or PuTTY on Windows) to connect to your Raspberry Pi. The default username is typically 'pi', and the default password is 'raspberry' which, as we'll see, is a significant security risk and needs to be changed immediately.
While SSH is powerful, its also a potential point of vulnerability. The default SSH configuration on a Raspberry Pi is not secure. The default username and password combinations are well-known, making the system easy to compromise if left unchanged. Furthermore, SSH can be exposed to the internet. Therefore, it is important to implement secure practices to protect your Raspberry Pi.
One of the most critical steps in securing SSH is to change the default password immediately. It's a simple but effective measure that prevents unauthorized access. Beyond that, it's highly recommended to generate an SSH key pair. This involves creating a private key, which you keep secure on your computer, and a public key, which you place on your Raspberry Pi. When you connect to your Pi, the SSH client uses the private key to authenticate, eliminating the need for password-based login. This is significantly more secure because it's virtually impossible to crack a well-generated SSH key pair.
Another important measure is to disable password authentication in the SSH configuration file ('sshd_config'). This forces users to use SSH keys for authentication, further enhancing security. You can also change the default SSH port (port 22) to a non-standard port. This won't eliminate the risk of a targeted attack, but it will help to reduce the number of automated attacks that scan for the default port.
Regularly updating your Raspberry Pi's software is another cornerstone of security. Keeping the operating system and all installed software up to date ensures that you have the latest security patches, which close known vulnerabilities. The Raspberry Pi OS, like any operating system, is constantly being updated to address security flaws. The update process is usually simple you can use the 'apt update' and 'apt upgrade' commands in the terminal. Its good practice to automate these updates, if possible.
Beyond SSH, Raspberry Pi Connect provides an alternative and often easier way to securely access your Pi. Raspberry Pi Connect offers a secure remote access solution specifically designed for the Raspberry Pi OS. It allows you to connect to your Raspberry Pi's desktop and command line directly from any web browser, eliminating the need to determine your local IP address or configure port forwarding. Raspberry Pi Connect, often activated in the configuration panel, simplifies remote access and provides a more user-friendly experience, especially for those new to the Raspberry Pi.
For more advanced users, securing your Raspberry Pi often involves connecting it to a Virtual Private Cloud (VPC), especially in IoT applications. This process establishes a secure and reliable connection between your Raspberry Pi and a virtual private cloud, ensuring that IoT devices can communicate with cloud services without exposing sensitive data. Connecting to a remote IoT VPC typically involves a few steps. First, you'll need to set up your Raspberry Pi with the latest version of Raspberry Pi OS and ensure it's fully updated. Then, youll need to establish a VPN connection. A VPN encrypts all the data transmitted between your Raspberry Pi and the VPC, ensuring that your communications remain private and secure. This is a crucial step if youre dealing with sensitive data or if you want to access your Raspberry Pi from anywhere in the world.
File sharing is another area where security is essential. Services like NFS (Network File System), SCP (Secure Copy Protocol), Samba, and Rsync allow you to share files between devices on your local network. While convenient, these services can introduce security risks if not configured properly. When setting up file sharing, it's important to restrict access to only authorized users and to use strong passwords. If you're using a protocol like Samba, make sure to keep it up to date to protect against security vulnerabilities. For file transfers, SCP is generally preferred over FTP (File Transfer Protocol) because it uses SSH to encrypt the data, making it much more secure.
The Raspberry Pi's default settings often prioritize ease of use over security. This means that many users, especially those new to the platform, might not be aware of the security risks involved. However, with a few simple steps, you can significantly harden your Raspberry Pi and protect it from unauthorized access. Changing the default password, generating SSH key pairs, disabling password authentication, keeping the system updated, and using a VPN are all essential practices. By implementing these measures, you can transform your Raspberry Pi from a potential security risk into a secure and reliable platform for your projects.
In conclusion, the security of your Raspberry Pi is not a set-it-and-forget-it task. It requires ongoing vigilance and a commitment to best practices. As new vulnerabilities are discovered, youll need to stay informed and adapt your security measures. By implementing the steps outlined in this article and staying up-to-date with the latest security recommendations, you can enjoy the versatility of your Raspberry Pi while safeguarding your data and your privacy. Remember, a secure Raspberry Pi is a productive Raspberry Pi.